When someone says to me 'I've found the silver bullet'...
'Silver weapons bear magical powers to conquer foes'. The proverb ascribed to the ancient Greek's Delphic Oracle has survived centuries to become a favourite selling pitch for information security tools.
Silver weapons, now like then, are a myth. Yet we information security professionals regularly encounter pitches selling intrusion prevention systems, threat intelligence, and other defensive technologies as a cure-all to complex problems.
Organisations, despite the marketing pitch, cannot hope to find security salvation in a box because effective protection is a complex and considered process. It is one of layered defenses that combines skilled humans with the knowledge that the defensive perimeter is perforated.
What might this look like? The answer differs between organisations and the resources they have.
Take a look at Google's BeyondCorp, for example. This 'zero trust' security framework spawned in the wake of the 2010 Operation Aurora has been built over years from the ground-up with a knowledge that high perimeter walls are insufficient to protect the organisation.
Or step back and consider the Australian Signals Directorate's much respected Top 4 Mitigation Strategies, a concept inked some years after my tenure at the agency. Here application whitelisting, application patching, operating system patching, and restricted administrative rights are king.
That list has been expanded just recently into the Essential Eight, a longer list that builds on the Top 4's defence against targeted threats to cover more common attacks.
Without these controls understood and in place, the best single security technology will be little more effective than rearranging chairs on the Titanic.
Reviewing security strategies and awareness training, something we do at Telstra, is of far greater importance than the search for the silver bullet.
So is knowing what is important. An organisation's security focus should centre on the customer, on the data, rather than systems. Here Telstra's Five Knows is useful to consider:
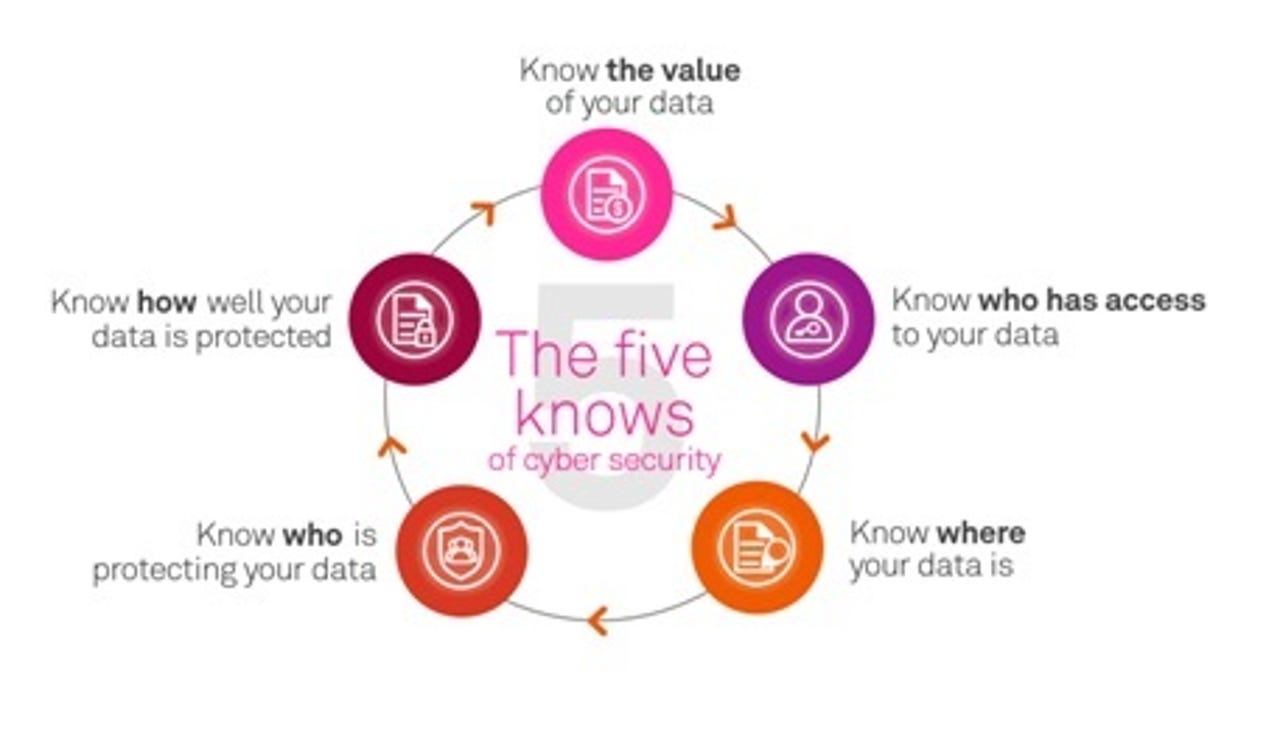
When fully considered, the Five Knows will help organisations find their critical data and understand the level of exposure and risk facing each data set.
This cannot be done overnight; it requires buy-in from business units across the organisation, effective security messaging and communication, and the resources to locate and protect critical data.
Proper security is a slow-moving machine fueled with careful understanding of risks and processes. No silver bullet can help.
For more on security download the full Telstra cybersecurity report.
Go to Telstra Exchange for more security.